تم بفضل الله تخريج دورة دبلوم القضاء السادسة حيث كان كان عدد الخريجين ٤٧ خريجا حيث حضر الحفل إضافة للخريجين وبعض الاخوة المدرسين ثلة من الفعاليات العلميةو الإصلاحية في المجتمع حيث ألقى مدير المعهد وممثل المدرسين وممثل الطلاب وبعض الضيوف كلمات عبروا فيها عن سعادتهم وسرورهم بهذه المناسبة ومدى أهمية المعهد ومساهمته في نشر ثقافة القضاء الشرعي وتاهيل الكوادر العلمية ...
أكمل القراءة »المعهد مؤسسة تعليمية، تأسس بتاريخ 17/5/1434هـ الموافق 29/3/2013م ويهدف إلى نشر المفاهيم الأصلية للقضاء الشرعي، ويسعى بعمله في تطوير عمل المحاكم الشرعية، ويرى أنه خطوة على طريق بناء مجتمع العدل وصيانة الحقوق، مركزا على إعداد وتأهيل القضاة العاملين في المحاكم. .. اقرأ المزيد
إعلانات المعهد
أحدث دورات الدبلوم القضائي
أحدث الدورات التخصصية والندوات القضائية
مختارات من فتاوى القضاء
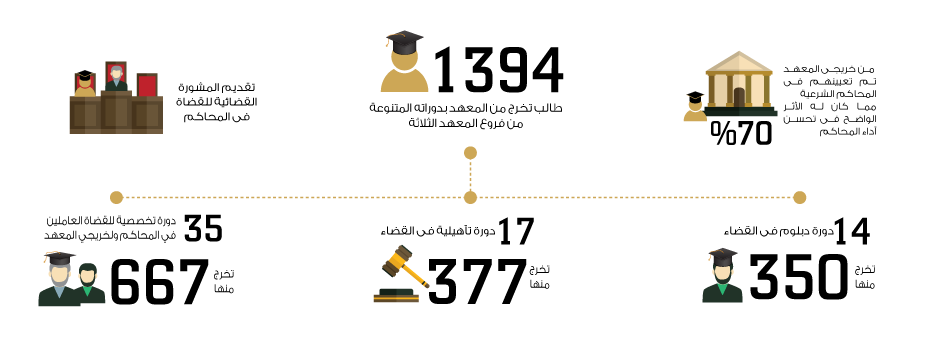
 معهد إعداد القضاة مؤسسة تعليمية مستقلة تهدف إلى نشر علوم القضاء الشرعي
معهد إعداد القضاة مؤسسة تعليمية مستقلة تهدف إلى نشر علوم القضاء الشرعي








